Adapting to the Unexpected: A Lesson in Cybersecurity Risk Management
July 27, 2024
'No Plan Survives First Contact With the Enemy', this saying, often attributed to military strategists, perfectly encapsulates a crucial aspect of cybersecurity: even the best-laid plans must adapt to unforeseen challenges. This principle is particularly relevant in risk assessment, where flexibility and strategic decision-making are key.
Recently, I was involved in a scenario that underscored this reality. An organization faced a critical decision after deploying a security patch to their Intrusion Prevention System (IPS). This patch was essential for addressing high and medium-risk vulnerabilities, safeguarding the organization's network. However, it also caused compatibility issues with a legacy payment processing application on a specific server, disrupting critical functions.
The organization had two main options:
-
Rolling Back the Patch: This would restore the application's functionality but reintroduce known vulnerabilities, potentially exposing the network to threats. It’s akin to removing a bandage from minor dents on the ship's hull—concerning but not immediately catastrophic.
-
Removing the Server from IPS Protection: This would isolate the problem, allowing the legacy application to function, but at the cost of exposing that server and potentially the entire network to attacks. This is like opening a hole in the ship's hull without protection, risking the safety of everything on board.
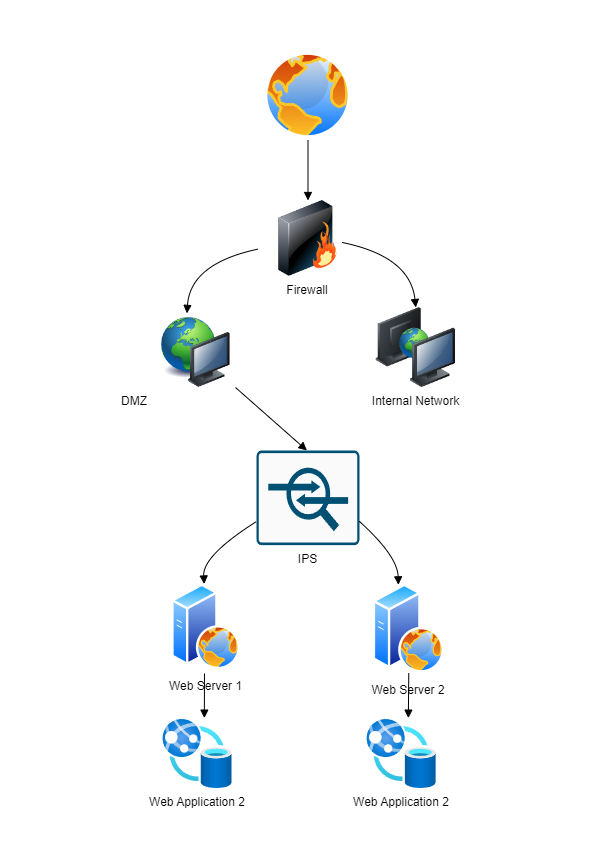
Analyzing the Trade-Offs: Faced with these options, the organization had to carefully weigh the trade-offs. Rolling back the patch might seem like a short-term solution, restoring full functionality but reintroducing vulnerabilities that could compromise the entire network. This approach might be necessary if the application is critical and downtime is not an option, but it requires immediate attention to implement a secure, long-term solution.
On the other hand, removing the server from IPS protection addresses the immediate compatibility issue without impacting the rest of the network. However, this exposes the server—and any connected data or systems—to greater risk. This decision is particularly dangerous if the server contains sensitive information or is crucial to the network's security posture. The decision must consider the potential impact on overall network security, the sensitivity of the data at risk, and the feasibility of implementing compensating controls to mitigate the increased risk.
Strategic Decision-Making in Cybersecurity: This scenario underscores the importance of a flexible and adaptive approach in cybersecurity risk management. More importantly, it highlights the need for strategic decision-making. Effective cybersecurity requires not just strong defenses but also the ability to make informed decisions under pressure. An IPS plays a crucial role in this by detecting and preventing common threats targeting web applications, such as SQL injection and cross-site scripting (XSS). These threats can compromise sensitive data and disrupt services, making IPS an essential component in maintaining the integrity and security of web applications.
Additionally, maintaining separate environments for production (PROD) and quality assurance (QA) allows organizations to test patches and updates without impacting live systems. This practice can prevent disruptions in production environments, ensuring that any issues are identified and resolved in a controlled setting before deployment.
Real-World Examples: The Marriott International Data Breach in 2018 serves as a cautionary tale. Attackers exploited vulnerabilities in less-secured network segments, specifically the Starwood Hotels reservation database, which was not as rigorously protected as other parts of the network. This breach led to the exposure of personal information for approximately 500 million guests, highlighting the dangers of under-protecting certain areas within a network.
Similarly, the Uber Data Breach in 2016 reminds us of the consequences of inadequate protective measures. Hackers accessed sensitive data stored on a third-party cloud service by exploiting weak access controls and a lack of segmentation. This breach affected 57 million users and drivers, emphasizing the importance of robust access controls and network segmentation, especially in cloud environments.
These examples remind us that cybersecurity demands more than just robust defenses; it requires strategic decision-making, thorough testing processes, and continuous adaptation. By being vigilant, adaptable, and prepared, we can navigate unexpected challenges and protect our assets in an ever-evolving threat landscape.
